A severe command injection vulnerability was just disclosed in a highly popular MCP server. Framelink's figma-developer-mcp package, with nearly 1 million downloads and over 11,000 GitHub stars, contained a flaw (CVE-2025-53967) that allowed attackers on the same network to execute arbitrary commands on the host machine.
This command injection vulnerability is made possible because the figma-developer-mcp server listens on an open port without authentication, the exact risk we highlighted back in April. In that post, we revealed how Chrome extensions and other devices on the local network could exploit unauthenticated MCP servers running on localhost, effectively breaking Chrome's sandbox model. Now we're seeing the consequences of that design flaw play out in real time: attackers can reach this vulnerable code precisely because there's no authentication barrier protecting the MCP server. The combination of unauthenticated access and exploitable code like command injection creates a perfect storm for remote code execution.

The Vulnerability
The vulnerability resides in the fetchWithRetry function located in src/utils/fetch-with-retry.ts, which initially tries to get content using the standard fetch API. When this request fails, commonly because of connectivity problems, SSL validation errors, or limitations imposed by corporate proxies, it falls back to running a curl command through child_process.exec.
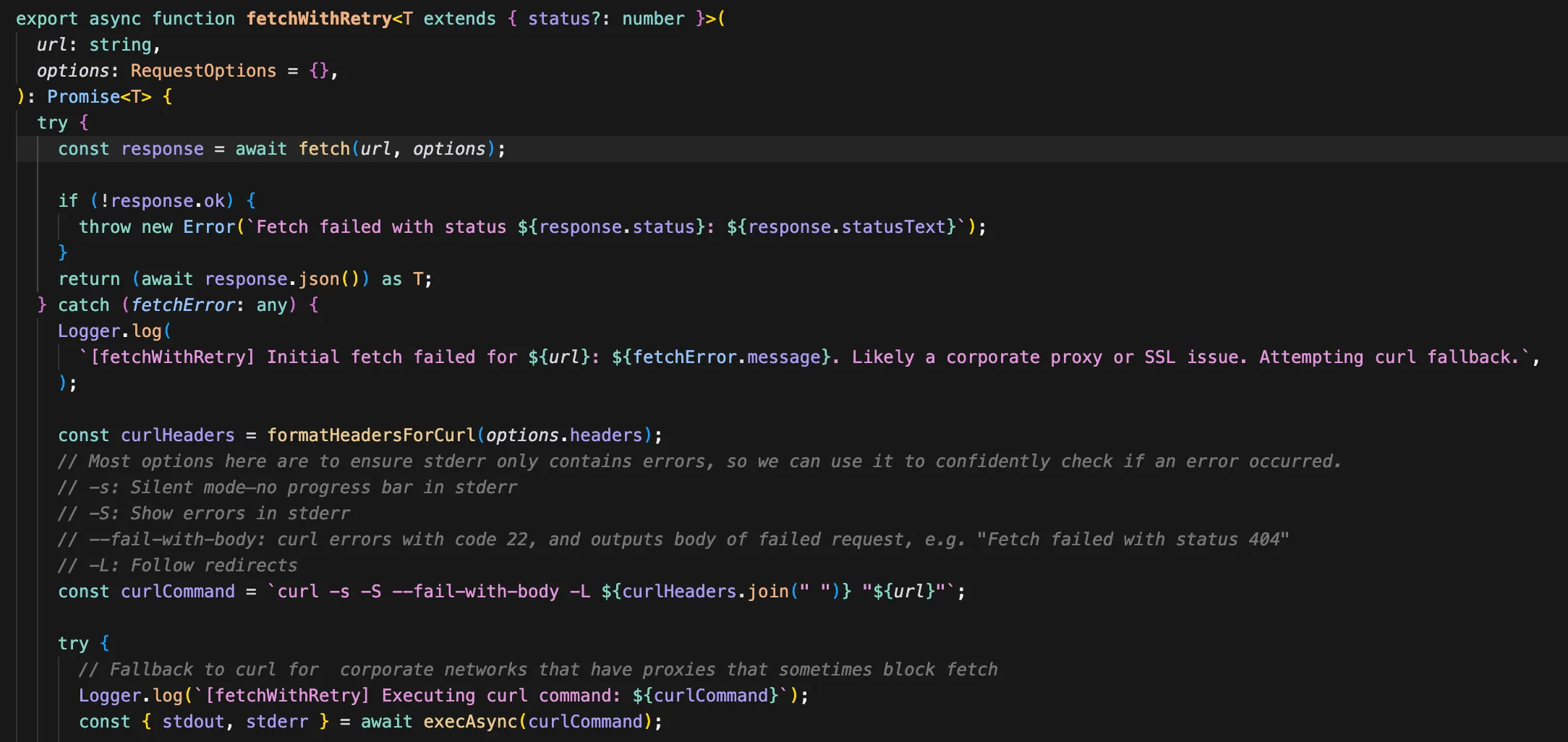
Here's the critical flaw: the curl command is built from untrusted input without any sanitization. This allows attackers to inject shell metacharacters like $(), |, ;, && that break out of the intended command and execute arbitrary code.
The vulnerable section of code is:
const curlCommand = `curl -s -S --fail-with-body -L ${curlHeaders.join(" ")} "${url}"`;Exploitation Flow
An attacker exploits this vulnerability in two steps:
- Session setup: The attacker issues an initialization request to the MCP server to obtain an
mcp-session-id. This session ID is required for ongoing communication with the server. Critically, this is not an authentication mechanism—anyone who can reach the server can obtain a session ID. - Invoking tools: With a valid session, the attacker submits a JSON-RPC call using the
tools/callmethod to trigger one of the exposed tools, such as:get_figma_data: Retrieves layout information about a Figma filedownload_figma_images: Downloads SVG and PNG images from Figma files
A malicious payload targeting get_figma_data might look like:
{
"method": "tools/call",
"params": {
"name": "get_figma_data",
"arguments": {
"fileKey": "$(id>/tmp/TEST)"
}
}
}This translates into a curl command that executes the injected id command and writes its output to /tmp/TEST. More sophisticated attacks could install persistence, download and execute malware, exfiltrate sensitive data, or deploy ransomware—all running with whatever permissions the MCP server process has.
Why This Is Accessible
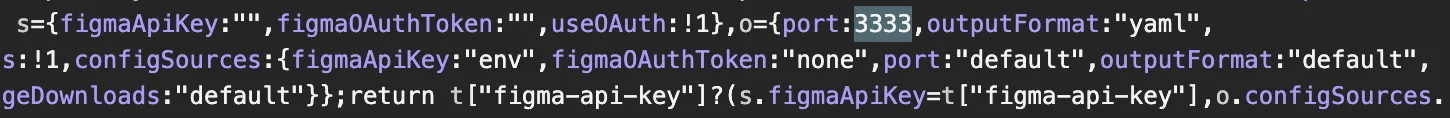
The MCP server runs locally and by default listens on port 3333 using app.listen() without defining a specific host address. As a result, the Express server is bound to 0.0.0.0 or ::, allowing access from any network interface instead of only localhost. This default behavior is poorly documented and significantly expands the attack surface.
Combined with the lack of authentication in the MCP protocol, this means anyone on the same network—such as users on shared Wi-Fi, compromised corporate machines, or even remote attackers using DNS rebinding techniques—can reach and exploit this vulnerability. This drastically expands the attack window beyond what most developers expect from a tool that's supposed to run locally.
The Growing MCP Security Risk
This isn't an isolated incident. The MCP ecosystem is expanding rapidly, thousands of servers offering powerful capabilities, but security practices haven't kept pace. Just in the past month alone, we've exposed two widespread malicious MCP servers in addition to this legitimate-but-vulnerable one. Developers are adopting these tools faster than they're being properly vetted, and the results are predictable: critical vulnerabilities and outright malicious packages in the wild, putting entire development environments at risk.
The problem isn't just individual bugs. It's the combination of systemic design flaws (like default unauthenticated access) and implementation mistakes (like command injection) that creates a compounding security crisis. As MCP becomes more embedded in AI-assisted development workflows, these vulnerabilities become entry points not just to individual machines, but to entire corporate networks and codebases.
Mitigation
This vulnerability was discovered by Imperva Threat Research in July 2025 and patched in version 0.6.3 (released on September 29, 2025). We recommend updating the package immediately and restarting all devices running this MCP to fully mitigate the risk.
IOCs
- NPM Package:
figma-developer-mcp - Vulnerable versions: < 0.6.3











%20copy.jpg)
