Half a million VKontakte users had their accounts silently hijacked. Their settings reset every 30 days. Automatically subscribed to groups they never chose. All through Chrome extensions that looked like simple VK customization tools.
We discovered a sophisticated malware campaign targeting VKontakte (VK), Russia's largest social network with over 650 million users. What started as a simple search for Yandex advertising code led us to uncover a network of five malicious Chrome extensions with over 500,000 combined installations.
This isn't just adware or a simple typosquat. This is active account manipulation - malware that:
- Automatically subscribes users to the attacker's VK groups (75% probability on each session)
- Resets account settings every 30 days to override user preferences
- Manipulates CSRF tokens to bypass VK's security protections
- Tracks donation status to gate features and monetize victims
- Maintains persistent control through multi-stage code injection
The attacker? A single threat actor operating under the GitHub username 2vk, using VK's own social network to distribute malicious payloads and build a follower base through forced subscriptions.
This is the story of how we tracked down the VK Styles malware network - and what it means for browser extension security.
The Discovery: Following the Yandex Trail
The trail didn’t start with Yandex - it started with our risk engine. It flagged a Chrome extension that was injecting Yandex display ad scripts into every page a user opened.
From there, we searched for other extensions using the same Yandex display framework. The search led us to VK Styles - a Chrome extension with 400,000 installations that claimed to be a simple VK customization tool. But buried in its code was something unusual: a Yandex metric ID calculated dynamically to avoid detection.
'R-A-' + 843079 * 2 // Evaluates to: R-A-1686158
Why calculate it? Because static analysis tools and security scanners search for exact strings. By computing the ID at runtime, the malware evades simple pattern matching.
But this calculation made us suspicious. So we digged deeper to the extension code
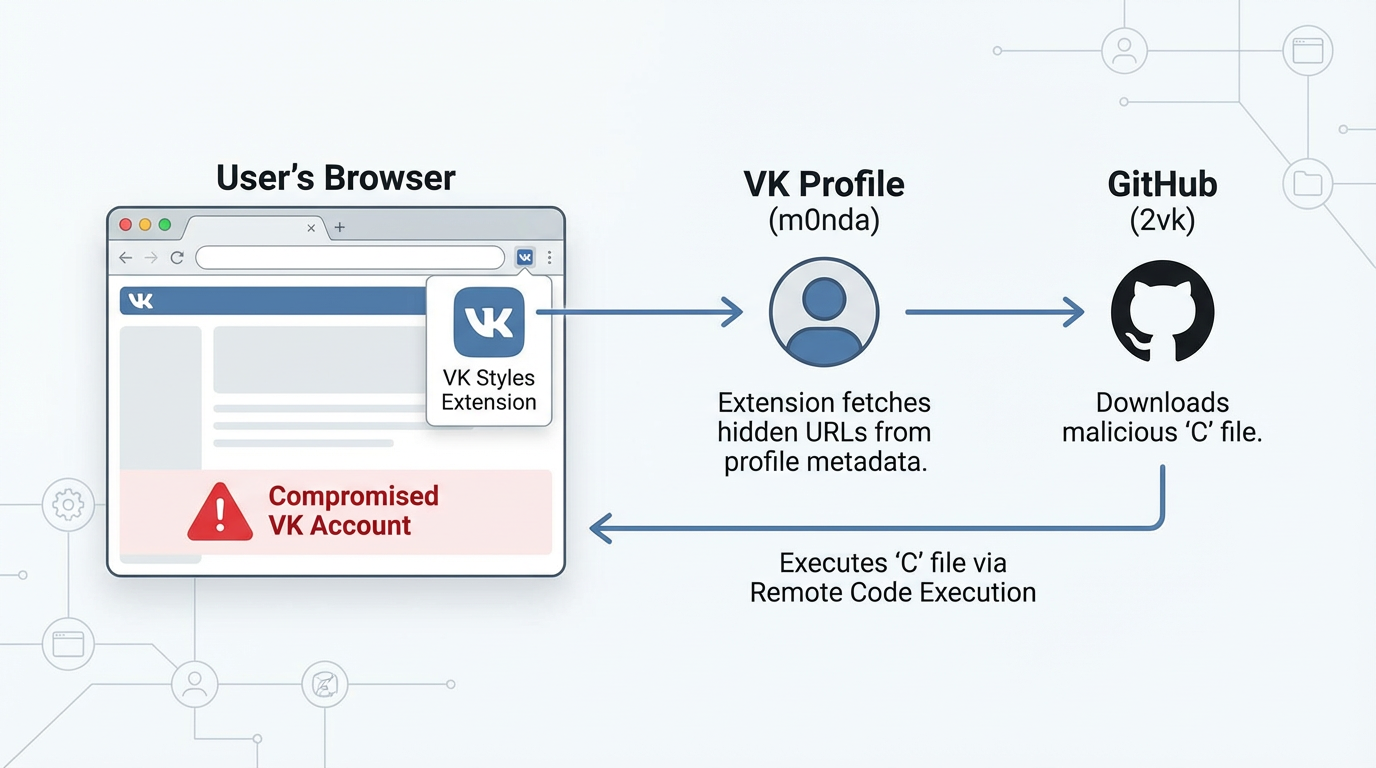
We found that the Yandex metric was just the surface. The real malware was multi-stage, using VK's own social network as infrastructure.
Stage 1: Two Lines That Changed Everything
The extensions themselves appear harmless. “VK Styles” promises to enhance your VK experience with custom themes, extra features, and a cleaner interface. It boasts thousands of positive reviews and receives regular updates - nothing in its Chrome Web Store listing raises immediate red flags.
But when we ran our agent on the VK Styles codebase, we found two lines, buried in separate locations, that changed everything.
.png)
Which is basically
.png)
This allowed any string passed to E to be executed. From there, the agent traced which components were invoking E and discovered code that pulled URL data from the metadata of a VK profile: vk.com/m0nda. The extension would download code from that profile and execute it locally.

This isn’t an ordinary VK account - it functions as the attacker’s C2 infrastructure, disguised as a personal social media profile.
The Metadata Payload
Hidden in the VK profile's HTML metadata tags is the next stage:
<meta name="description" content="4000 :: G2vk.github.io/-/ V1.0.250.69 Yan.yandex.ru/system/context.js Ayastatic.net/partner-code-bundles/ :">
At first glance? Gibberish. But decode it:
G (GitHub): https://2vk.github.io/-/
Y (Yandex): https://an.yandex.ru/system/context.js
A (Ad bundles): https://yastatic.net/partner-code-bundles/
V (Version): 1.0.250.69
The attacker is using VK's meta tags as a dead drop for payload URLs.
Why is this clever?
- No hardcoded URLs in extension code - harder to detect and block
- Dynamic updates - attacker can change payloads by editing their VK profile
- Legitimate infrastructure - VK.com itself serves the C2 coordination
- No suspicious external domains - everything looks like normal VK traffic
The extension fetches the VK profile, parses the meta tags, extracts the encoded URLs, and downloads the next stage from GitHub.
Stage 2: The GitHub Payload
The GitHub account 2vk hosts the actual malware: https://github.com/2vk
The repository name is “-” , yes just a hyphen
The repository contains a file simply named C - innocuous, unsearchable, deliberately vague. Inside is obfuscated JavaScript that gets injected into every

VK page the victim visits.

Summary of the flow:
We analyzed all 17 commits of this file, spanning from June 2025 to January 2026. What we found was a malware operation that evolved over time, adding features, refining techniques, and becoming more aggressive with each update.
Code Evolution Timeline
June 22, 2025 (Commit 9c04efc) - Initial version
- CSRF cookie manipulation implemented
- Basic VK API wrapper functions
- Core infrastructure established
December 23, 2025 (Commit ba0125b) - Major malicious update
- Auto-subscription feature added (75% probability)
- 30-day settings reset introduced
- Forced configuration overrides
January 13, 2026 (Commit 8f94054) - Monetization upgrade
- Changed from HTML scraping to direct API calls
- Donation tracking via VK Donut API
- Feature gating based on payment status
January 2026 (Commit c9d1e96) - Stealth improvements
- Removed 100+ lines of IntersectionObserver code
- Streamlined to reduce detection surface
- Continued version bumps and selector updates
Each commit shows deliberate refinement. This isn't sloppy malware - it's a maintained software project with version control, testing, and iterative improvements.
The Silent Takeover: What This Malware Actually Does
Once fully deployed, the malware performs five categories of malicious actions. Let's break them down.
Auto-Subscription: Building an Army
The Code:
.png)
Translation: There's a 75% chance (3 out of 4 random outcomes) that every time you visit VK, the malware automatically subscribes you to VK group -168874636.
What's VK Group 168874636?
It's the attacker's own group: https://vk.com/club168874636.
This redirects to VK Styles (https://vk.com/2style) - the "official community" for the malware disguised as a user support group. That has 1.4M followers , such as popular guy VK Styles:)
Why is this brilliant?
- Viral growth - Every victim becomes a subscriber, boosting the group's legitimacy
- Social proof - "1.4M members can't be wrong!"
- Free advertising - Victims' friends see them joining, adding trust
- Monetization - More followers = more influence = more victims
- Persistence - Even if you unsubscribe, there's a 75% chance you'll be re-subscribed on your next VK visit
The attacker turned malware distribution into a self-reinforcing cycle. The victims themselves advertise for more victims.
The 30-Day Reset: Persistent Account Control
The Code:
.png)
Translation: Every 30 days (2592e6 milliseconds = 30 days), the malware:
- Resets your VK feed sorting to "recent" instead of algorithmic
- Changes your message bubble theme to theme 0
- Overrides any custom settings you've configured
- Tracks the last reset timestamp to ensure it happens every month
CSRF Token Manipulation: Breaking VK's Security
The Code:
.png)
Translation: The malware can read and manipulate VK's CSRF protection cookie remixsec_redir.
What's a CSRF Token?
Cross-Site Request Forgery (CSRF) tokens are security mechanisms that prevent unauthorized actions on your account. When you perform a sensitive action on VK (like changing settings or posting), VK checks this token to make sure the request actually came from you and not from a malicious site.
By manipulating this cookie, the malware can potentially:
- Bypass CSRF protections when making API calls
- Perform actions that would normally be blocked
- Make requests appear legitimate to VK's security systems
This is a direct attack on VK's security infrastructure.
The Network: Five Extensions, One Threat Actor
Searching for the Yandex metric ID R-A-1686158 revealed a network of extensions, all controlled by the same threat actor, all using the same infrastructure:
- Total confirmed victims: 502,000
- One extension was already removed by Google in 2024 for Web Store policy violation - evidence that this campaign had been detected before but the threat actor simply pivoted to new extension IDs and continued the operation.
- The most popular extension,
VK Styles – Themes for vk.com, was removed from the marketplace on February 6.
Total: 502,000+ confirmed victims
VK Group Membership: The attacker's VK Styles group has grown organically through forced subscriptions, creating a self-sustaining infection vector.
Geographic Distribution: Primarily Russian-speaking users (VK's core demographic), but also users across Eastern Europe, Central Asia, and Russian diaspora communities worldwide.
Duration: Campaign active since at least June 2025, with continuous updates through January 2026 - over 7 months of active operation.
What's Happening Right Now
Every day, thousands of VK users:
- Are unknowingly subscribed to the attacker's group
- Have their account settings reset
- Have their CSRF tokens manipulated
- Are being monetized through the donation tracking system
- Are serving as distribution nodes for the malware
And because the extensions update automatically, the attacker can push new malicious code to all 500,000+ victims instantly, with no user interaction required.
Final Thoughts
This research was conducted by the team at Koi, driven by our commitment to uncovering threats hiding in the software supply chain.
The VK Styles campaign demonstrates several emerging trends in browser extension malware:
1. Social Networks as C2 Infrastructure Using VK profiles, meta tags, and legitimate social platforms to coordinate malware is brilliant and terrifying. It's free, it's trusted, it's hard to block.
2. Self-Propagating Through Forced Actions Auto-subscribing victims to attacker-controlled groups creates a viral distribution mechanism that feeds on itself.
3. Subscription-Based Malware Business Models Monetizing malware through "premium features" while keeping the infection active is a new evolution of ransomware tactics.
4. Persistence Through Periodic Resets The 30-day reset cycle ensures victims can never fully escape the malware's control without removing the extension.
5. Multi-Stage, Dynamic Payloads By fetching payloads from external sources (GitHub, VK profiles), attackers can update their malware without touching the extension code itself.
Browser extensions have become one of the most dangerous attack vectors in modern security:
- They run with high privileges
- They auto-update without user consent
- They're hard to monitor and audit
- Marketplaces have limited security vetting
- Users trust them implicitly
This is why we built Koi. Our platform discovers, assesses, and governs all software that flows into your environment - including browser extensions that traditional security tools miss entirely.
Trusted by Fortune 50 organizations and some of the largest tech companies in the world, Koi helps security teams gain visibility into the software their developers and employees actually use.
Book a demo to see how Koi can protect your organization from the threats hiding in browser extensions, npm packages, VS Code extensions, and the entire marketplace ecosystem.
Because when malware can hijack half a million users through extensions that look completely legitimate, you need tools that watch what software actually does - not just what it claims to be.
Stay safe out there.
IOCs
ceibjdigmfbbgcpkkdpmjokkokklodmc(400,000 installs)mflibpdjoodmoppignjhciadahapkoch(80,000 installs)lgakkahjfibfgmacigibnhcgepajgfdb(20,000 installs)bndkfmmbidllaiccmpnbdonijmicaafn(2,000 installs)pcdgkgbadeggbnodegejccjffnoakcoh(2,000 installs)










%20copy.jpg)


